Despite substantial industry concerns about the growth and progress of Quantum Computing, a Quantum Computer capable of breaking cryptosystems might be three to five decades away, claimed one panel at a recent conference.
By Daksha Bhasker, CISSP
 Earlier this year I was able to attend the RSA conference in San Francisco. Looking back at some of what I took away from this event, one of the standout sessions looked at the highly debatable topic of cryptography.
Earlier this year I was able to attend the RSA conference in San Francisco. Looking back at some of what I took away from this event, one of the standout sessions looked at the highly debatable topic of cryptography.
The Cryptographers' Panel is a well known fixture in the RSA schedule which, year after year, has brought together the great cryptographers and mathematicians of our time. This year the panel was moderated by Whitfield Diffie and featured RSA's own Adi Shamir along with:
- Clifford Cox, former chief mathematician at the U.K. Government Communications Headquarters (GCHQ)
- Ann Dames, distinguished engineer at IBM Infrastructure working on post-quantum cryptography (PQC)
- Radia Perlman Fellow at Dell EMC who specializes in network security
The panelists engaged in a lively debate on quantum computing sprinkled with plenty of humor on the hype around it.
Promises, Not Solutions
Shamir pointed out that over a span of thirty years, since the 1990s, quantum computing has only produced promises and, to date, is incapable of solving a single practical problem faster than classical computers.
Perlman's guidance was to think about the threatened systems which are primarily public key systems, to a lesser extent impacts to symmetric keys and hashing functions resulting from Grover's algorithm. To support, below is a table from NIST's report on post-quantum cryptography summarizing the Impact of Quantum Computing on Common Cryptographic Algorithms with possible countermeasures.
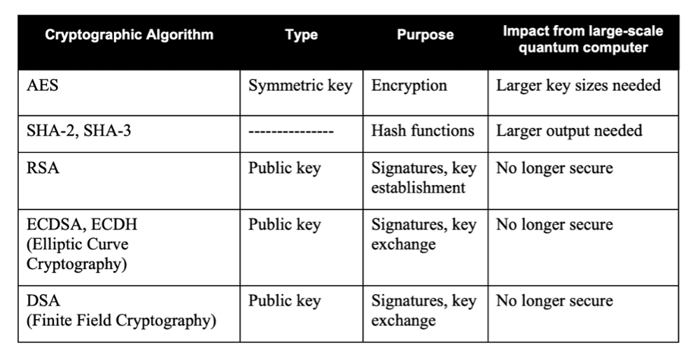
Diffie expressed that RSA, Diffie-Hellman and Elliptic Curve cryptography (ECC) being threatened by quantum computing was purely the imagination of the physicists.
The panel generally felt that a quantum computer capable of breaking cryptosystems might be over 3-5 decades away, citing the extremely slow progress trajectory of quantum computers to date. To illustrate, Shamir referenced Yale researchers that had succeeded in extending the life of a qubit in storage, from 1 millisecond to 1.8 milliseconds. This is not significant enough, as in order to factorize 2048 bit RSA, computation may need to be conducted for days – and, to run Grover's algorithm, it might need to run for years.
While the progress of quantum computers is being tracked mainly by the number of available qubits, issues such as quantum volume or quality, performance (the time taken to solve a problem) and the problem of decoherence are far from being solved. These factors are essential for quantum computers to deliver on their promise.
According to the panel, since the NSA and NIST perceive the threat of quantum computers and are calling for adoption of quantum resistant algorithms, there is significant likelihood that we might face requirements for designing systems that call for quantum resistant algorithms even if quantum computers do not arrive any time soon.
They briefly discussed PQC algorithms selected by NIST, one for general purpose public key encryption CRYSTALS-Kyber and three for digital signatures and identity verification (CRYSTALS-Dilithium, Falcon and SPHINC+) that will be integrated into NIST standards by 2024. The panel cautioned that each algorithm has their respective pros and trade-offs, which should be considered specifically for each use case per requirements. Shamir opined that, of the three digital signatures, he would recommend only SPHINC+, since it has the highest signature size and offers the highest security level.
Where Is The Functional Security Need?
The major point to consider is that our everyday communication and data transmissions do not require secrecy of 50 to 100 years. For data transmission that does require secrecy, the recommendation is to observe the most conservative approach to security: use algorithms with the highest level of security, do not use public key cryptography, use classical cryptosystems, and go through the hassle of manual exchange of keys.
Other topics discussed included the tenth anniversary of Edward Snowden's disclosures, the use of artificial intelligence (AI), machine learning (ML) and chatbots for human engineering which can make social engineering attacks much more believable with flawless English. Also, the use of AI/ML to improve both defensive and offensive security tools and tactics.
In summary, the panelists made an effort to debunk the hype of quantum computers, the predicted timelines of arrival and the overall capabilities of the technology. The message to cybersecurity professionals is to prepare to design systems using quantum resistant cryptography (QRC) as per guidance from NIST even if quantum computers do not arrive. The guidance is to choose purpose specific QRC wisely based on the risk posed to the specific system and its data.
There is a cautionary note for new cryptographic systems that have yet to stand the test of time, citing the PQC candidate SIKE that was cracked in around an hour with a classical computer. The panelists encourage practitioners to consider the strength of the QRC algorithms, levels of security offered, the effort needed to potentially crack based on algorithms (structured lattices, hashing), their characteristics for efficiencies, floating point requirements, key sizes, large signatures and apply them by use case requirements.
Daksha Bhasker has over 20 years of experience in technology and telecommunications service provider industries. She's held roles in both business management and technology development, accountable for complex solution architectures and security systems development. Daksha's security work spans carrier scale voice, video, data, and security solutions.


