By Enoma Odia, CISSP, ISSMP, CSSLP
Cybersecurity is a crucial concern for modern organizations due to the rise of increasingly sophisticated cyber threats and attacks. Implementing cybersecurity controls and managing the escalating risk presents considerable challenges for organizations, especially considering the potential financial implications. It is why collaboration is a preferred approach, allowing cost and workload to be diluted to more manageable levels.
While cybersecurity collaboration is not a novel concept, government agencies like ENISA and CISA-ISACs are primarily tasked with promoting collaboration to bolster cybersecurity resilience. Notwithstanding, these agencies often rely on information sharing on emerging threats, vulnerabilities, and best practices as their primary approach.
Although beneficial, this passive approach does not sufficiently improve cyber resilience. Additionally, many organizations depend on cybersecurity frameworks for protection. Despite their effectiveness when correctly applied, these frameworks are not inherently designed for cybersecurity collaboration, thus limiting their utility in a cooperative context for securing an entire sector or associated third parties.
To address these limitations, this blog proposes – in two parts – a novel approach to augment cybersecurity resilience by integrating the cybersecurity framework into a cooperative model. This approach, known as the Sector-wide Integrated Cyber Defense Approach (SICDA), is intended to enhance cybersecurity across an entire industry, considering that organizations within a sector likely face similar cyber threats and challenges.
Drawing from conventional warfare tactics where allies collaborate for collective defense against adversaries, SICDA introduces an active defense approach for the industry. It builds on existing cybersecurity frameworks to ensure its acceptability among industry members. The blog will further elucidate the specifics of the SICDA approach.
How does SICDA work?
SICDA works by rallying organizations around Accountable Cybersecurity Organizations (ACOs). ACOs serve as the backbone of the SICDA model, pooling resources and intelligence to strengthen the sector's cybersecurity defenses.
Each ACO would comprise several organizations from the same industry sector or geographical location. These organizations would contribute to a shared pool of cybersecurity resources, including intelligence, technology, and human resources. The ACO would then manage these pooled resources, leveraging them to implement coordinated cybersecurity strategies for all member organizations.
Furthermore, SICDA suggests the integration of Managed Security Service Providers (MSSPs) into the collaborative model. MSSPs, with their specialized expertise and capabilities, can provide comprehensive cybersecurity services to the ACOs, thereby supplementing the ACO's capabilities and ensuring a robust, responsive defense against cyber threats.
In this way, SICDA fosters a proactive, integrated, and sector-wide approach to cybersecurity, leveraging the collective strength of multiple organizations to improve the resilience and efficacy of cybersecurity defenses.
Challenges: Cybersecurity Collaboration
The current landscape of cybersecurity collaboration primarily revolves around passive defense strategies centered on information sharing. An example is the Cybersecurity and Infrastructure Security Agency (CISA), which collaborates with over 13,000 organizations, providing tools, resources, and defense services. However, it is essential to note that CISA primarily focuses on information sharing rather than proactively safeguarding organizations. Additionally, its 24/7 operation center mainly serves as a platform for sharing information to protect these organizations. A 2018 paper by the European Union Agency for Cybersecurity (ENISA) titled "Information Sharing and Analysis Centers (ISACs) Cooperative Models" identifies several challenges within the realm of cybersecurity collaboration. These challenges include:
- Lack of resources: "the industry is not willing to share experts and appoint them to work for ISACs."
- Weak capacity in analysis role "Because of the overall lack of resources and IT security experts it becomes challenging for ISACs to strengthen its analysis role."
- Not enough funding: "lack of funding is a general problem for the ISACs. It keeps the member organizations from hiring experts who could work in ISACs themselves."
- Qualitative evaluation of ISAC activities is difficult: "Most ISACs face the challenge of evaluation. It is difficult to identify clear failure and success factors."
- Duplication of information: "due to the existence of many information sharing-groups, the same information is usually passed through different sources."
- Inter-ISAC cooperation: "sharing best practices on areas such as governance and information sharing models, could benefit the development of ISACs in general."
- IT tools affecting data integrity: "The choice of the right tools to use to ensure data integrity is also a challenge for many ISACs. If the ISAC doesn't have enough funding, it is difficult to acquire specialized tools for information sharing and for data analysis."
These constraints impede the effectiveness of Information Sharing and Analysis Centers (ISACs). Furthermore, most cybersecurity frameworks do not advocate for collaboration or provide a systematic approach to facilitate collaboration across multiple organizations. Notably, even highly embraced standards such as NIST, which serve as a cornerstone in cybersecurity implementations, do not inherently address the applicability of cybersecurity collaboration across their domains as it is almost impossible to use the framework as means for organizations to work together to improve industry cybersecurity. The table presented below serves as an illustrative example highlighting this challenge i.e.,the proposed categories do not provide room for collaboration.
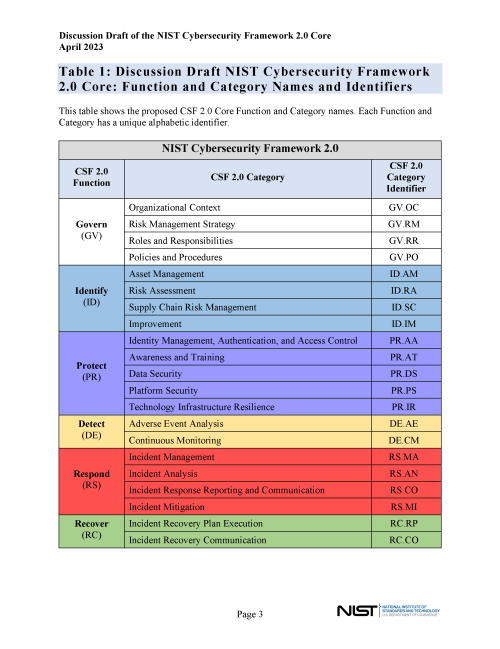
The root causes of the gaps identified in the table are due to several problems, and here are some potential factors that might be contributing to the issues:
- Competition and proprietary interests: In many industries, companies are hesitant to share information that could give their competitors an advantage. This can include cybersecurity strategies and insights, which may be viewed as proprietary.
- Lack of common standards or frameworks: Without industry-specific standards or frameworks, it can be difficult for companies to collaborate on cybersecurity. This could explain why the NIST CSF, while widely accepted, may not be fully effective in promoting collaboration.
- Regulatory constraints: Privacy regulations and other legal constraints can limit the extent to which companies are able to share information about cybersecurity incidents and threats.
- Lack of trust: Organizations might be reluctant to share sensitive information about their cybersecurity practices and incidents due to fears of reputational damage or concerns about how the information might be used.
- Resources and capabilities: smaller organizations might lack the resources or capabilities to participate fully in collaborative efforts. This can lead to a disparity in the level of collaboration across different companies within an industry.
- Absence of a collaborative culture: Industries that have traditionally operated in silos might lack a culture of collaboration, making it more difficult to establish collaborative cybersecurity efforts.
- Misaligned incentives: If the costs of collaboration (such as time, resources, or potential risks) are perceived to outweigh the benefits, companies may be less motivated to participate.
- Inadequate role of ISACs: As noted above, ISACs are not fully addressing the collaboration gaps in some areas. This could be due to a variety of factors, such as a lack of resources, insufficient participation by members, or a focus on other areas.
Amplifying our defenses against cyber-attacks calls for a unified effort across an entire business sector. Unfortunately, a common tool for managing cybersecurity risks, the NIST framework does not promote an active, cooperative form of defense. As a result, organizations face the twin burdens of implementing robust cybersecurity controls individually while also contributing to collaborative initiatives. This dual role is expensive and resource-intensive, placing extra strain on organizations as they strive to safeguard against cyber threats.
In the Part Two of this blog, I will continue the analysis of the SICDA framework and demonstrate how organizations can benefit from its use.