Key to an organization’s resilience is its ability to respond to an incident. As delegates at ISC2 Security Congress 2024 leaned, weak incident response plans can undermine recovery and other cybersecurity actions.
 How will your organization respond to a cyberattack when (not if) it
happens? At ISC2 Security Congress 2024 in Las Vegas, John Hollenberger,
CISSP, Lead Consultant at FortiGuard Proactive Services presented
Common
Incident Response Plan Shortcomings. Hollenberger discussed the
common characteristics of inadequate incident response plans (IRPs) and how
to address them.
How will your organization respond to a cyberattack when (not if) it
happens? At ISC2 Security Congress 2024 in Las Vegas, John Hollenberger,
CISSP, Lead Consultant at FortiGuard Proactive Services presented
Common
Incident Response Plan Shortcomings. Hollenberger discussed the
common characteristics of inadequate incident response plans (IRPs) and how
to address them.
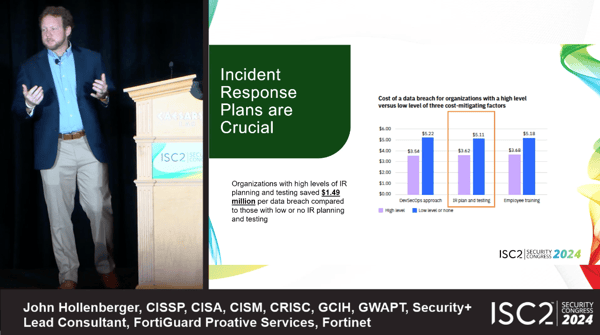
IRPs are step-by-step guides on how to deal with cyberattacks and their aftermath. Every detail must be considered, including the severity level of the attack, what responses must be made and when, who is in charge, and how to communicate what happened. To emphasize the importance of a solid IRP, Hollenberger noted that according to IBM’s 2024 Cost of a Data Breach Report, organizations with high levels of incident response (IR) planning and testing saved $1.49 million per data breach compared to those with low or no IR planning and testing.
The Five Common Mistakes in IRPs
Hollenberger identified the five most common mistakes in an inadequate IRP:
- Lacking a Charter – A charter is the more formal section of the IRP that defines, among other things, the purpose, scope, stakeholders, and the IRP itself. Among the most important things charters do is to identify single decisionmakers for each key step to ensure action is taken. He pointed out that decision making by committee absolutely does not work during a cyberattack. Another important job of the charter is to identify other staff that can rotate into key positions to avoid burnout during long running events.
- Lacking Authority or Limitation of Authority – Citing examples such as teams not being able to take actions without written permission from the CTO, he illustrated the need for each responsible party designated in the charter to have full authority to act when responding to cyberattacks, without the need to wait for authorization and wasting precious time.
- Lacking Management or Executive Commitment –The complete support of the leadership team enables incident response teams to fully commit to fighting cyberattacks, sometimes while foregoing their day-to-day responsibilities in the process. Without this support, incident response teams are unable to effectively respond.
- Lacking Communication Guidance –There are four forms of communication that need to take place during and following a cyberattack: internal to the organization; external to vendors, third parties, and the public; media communications; and, sometimes, communications to law enforcement. It’s critical that the who, what, and when of each type of communication is clearly outlined. When communicating with the media, having spokespeople who have received media training is very important, and having external and internal media communication templates can enable organizations to quickly respond to inquiries.
- Lacking Severity Levels and Escalation Procedures – Using the analogy of firefighting, Hollenberger described three levels of cyberattack severity. A low-level incident could be likened to a small brush fire that can be dispatched with minimal equipment and firefighters. A mid-level attack is like a small house fire that requires the assistance of more equipment and firefighters. And a high-level attack is similar to a multi-alarm apartment fire that affects hundreds of people and requires a massive turnout of emergency responders. By identifying and naming the levels of cybersecurity attacks in their IRPs, organizations can address each level with the appropriate response.
Where to Start?
In response to an audience question, it was suggested to search online for IRP templates or use those available from the NIST website. However, Hollenberger was quick to emphasize that a template is only the beginning and that templates need to be customized for each organization to be truly effective.
That point was again touched on when examining the shortcomings of some IRPs, with using off-the-shelf templates that haven’t been tailored to an organization’s specific needs being singled out as a common cause of problems. “This could be done because of a lack of knowledge or awareness about IRPs, or it could also be because organizations are simply ‘checking the IRP box’ in order to pass an audit or obtain cyber insurance,” it was noted.
Nonetheless, CISA and NIST were still recommended as great places to start the search for resources. Hollenberger also suggested that teams rely on external support and cross-train within their organizations to enable other employees to contribute to the response.
- Register now for ISC2 Security Congress 2025 in Nashville
- Develop your incident response skills with the ISC2 Incident Management: Preparation and Response Certificate
- Continuous Monitoring and Incident Response for Zero Trust


.jpg?h=420&iar=0&w=420)