Asad Rathore, CISSP, has managed multiple data platforms containing sensitive data for various financial and aviation organizations. Most of those data platforms reside on cloud infrastructure, with numerous endpoints, any of which might be vulnerable to a nefarious actor. He explains the notion of a data fortress, applying the defensive and operational concepts of the medieval castle to modern IT environments, to deliver robust perimeter security and internal policing.
Disclaimer: The views and opinions expressed in this article belong solely to the author and do not necessarily reflect those of ISC2.
Over a long period of time, I have repeatedly researched various data protection frameworks and consulted multiple data protection specialists. In that time, I have always come to the same conclusion: that I must fortify any data platform for which I’m responsible, as much as possible.
As an avid reader of history, I found myself drawn to the idea of the medieval fortress. The concept resonated with me because of the significant parallels with the data governance and protection frameworks and advice that I had received. In turn, this led to a decision to design and architect the safeguards of my data platform like those of such a fortress. Medieval castles and fortresses were built primarily to safeguard the treasury and the key people in a town. What if I could replicate such an objective, and build a data fortress that would protect the key asset (i.e., data) that resides on the platform? Here’s the story of the first time I used the approach.
The Data Fortress
My experience is that the most important step is to ensure that protective security controls are implemented – so I decided to implement just-in-time (JIT) access and role-based access controls. These would act as frontline safeguards, a metaphorical drawbridge to ensure that only authenticated, authorized actors can enter the data fortress and then only for a limited time.
I faced significant challenges implementing JIT access. These included convincing the board, drafting policies and piloting such an access policy. Decision-makers did see a benefit of implementing JIT access but, during the pilot, many users complained about the need to seek permission to re-login to systems after the expiry of the 15-minute window we had implemented. With this considered as too disruptive and problematic for the users of the applications, we subsequently agreed to a 30-minute access period. However, we also noticed a 60% decrease in the number of logins from users who had no relation with a production application.
Creating a Moat
I also decided to strengthen the firewall. In the fortress analogy this performs the function of a moat, ensuring that data is not lost and enabling inspection of all data is coming and in and out of the fortress, since it must do so via the main gate. I implemented next generation firewalls which enhanced the security barrier between our data platform and the outside world. The antivirus, anti-ransomware and anti-spam protection and endpoint security functionality that we implemented reduced by 20% the number of such potential attacks.
After an actor is authorized and permitted to enter the data fortress, such an actor can only access the applications for which they are authorized. For example: if the actor wished to access files or send out emails, the firewall played the role of preventing data loss and ensuring there wasn’t any unauthorized exfiltration. In the analogy with the medieval fortress, this is similar to guards checking for items or goods that someone is trying to move out of the castle.
Permission by Role
This is where I decided to implement role-based access control for applications. This was a massive exercise: obtaining all the user permissions to applications and ensuring the right user groups had the right access took a lot of testing and effort. In the beginning, we had to test via a pilot whether the right access group had the right access. There were frequent disputes with regards to what sort of accesses a user group should have, but these were resolved by the risk teams and the stakeholders during the pilot implementation.
Actors would be viewing the dashboards that they were permitted to access or they would be filling in forms to ensure data is entered correctly. I had to ensure that the forms were structured in a way where only the required information can be put which is based for a specific purpose, meeting the requirements of purpose limitation and data minimization for data governance.
I made sure that other safeguards such as sanitized views (i.e., views that show only the information that needs to be shown to the authorized person), row-level security and column-level security were implemented, providing additional security parameters to ensure that sensitive information and data was protected and is not exposed unnecessarily. I implemented the latest transport layer security (TLS) to ensure encryption in transit, in use and transparent data encryption (TDE) to ensure that we have encryption at rest.
To continue the fortress analogy, these safeguards provide a similar role to guards who escort coin from the treasury to other areas of the fortress. The data steward plays a key role to ensure that the data quality is maintained and that the asset are classified properly so that they can be stored, secured and protected accordingly.
Bringing in External Advice
We hired data governance consultants to ensure that proper data governance practices were implemented. We classified data assets by data sensitivity and data owners which took a lot of time as there were conflicts amongst owners as to which data assets were owned by which stakeholder group (data owner). This was resolved via workshops and by agreement by the stakeholders. Data stewards were nominated and trained. A data catalogue was crafted based on agreed terminologies. The data stewards ensured that data owners could collaborate and access the data accordingly and ensured that the data assets were compliant with the relevant regulations. Compliance plays a key role to ensure that the latest polices with regards to safeguards are being implemented. That helps with to maintain an adequate standard of safeguards.
The data governance controls that we applied improved data quality by 40%; end users received better insights and were making better decisions which helped increase the revenue stream for the organization. This approach to data governance was taken from the medieval fortress idea in which royal accountants and finance ministers used to work with security to ensure that funds were safeguarded and available to the respective departments, to keep the kingdom running!
This diagram shows the data fortress in its entirety.
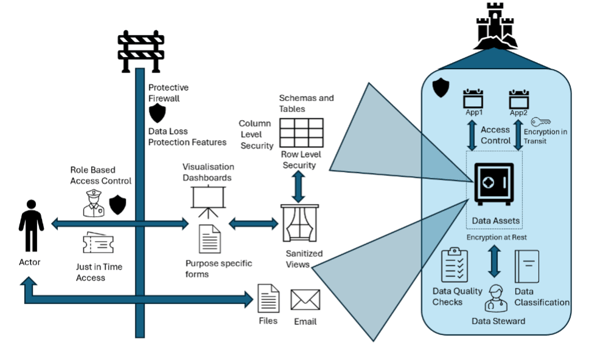
For me, the idea of the data fortress has played an important role in enabling data protection and governance, as it establishes a structured framework for managing, protecting and using data effectively across an organization. It ensures data quality, security and compliance with regulations, while also promoting operational efficiency and informed decision-making. I’ve used the playbook and blueprints of designing and implementing a data fortress at various organizations and so far have been fortunate not have encountered a single data breach.
Of course, I update the data fortress ‘playbook’ with the latest trends and technologies to ensure that the safeguards and practices are up-to-date. I’ve learned how, without proper data protection and governance, organizations face significant risks such as poor data quality, security breaches, regulatory fines and missed opportunities. By implementing robust safeguards, businesses can maximize the value of their data, reduce risks and build trust among stakeholders. Ultimately, it supports long-term success and growth.
Asadullah Rathore, CISSP, has 20 years’ experience of managing data platforms, data governance and cyber security. He has held management and technical roles, with responsibility for modernizing and protecting data platforms and assets. His cybersecurity work spans over 10 years for global financial, aviation and government organizations.
Related Insights